A Key That Is Generated By A Symmetric Cryptographic Algorithm
Cryptography
- A Key That Is Generated By A Symmetric Cryptographic Algorithm Is Said To Be A
- A Key That Is Generated By A Symmetric Cryptographic Algorithm Is Said To Be A
- A Key That Is Generated By A Symmetric Cryptographic Algorithm Is Said To Be A:
Derrick Rountree, in Security for Microsoft Windows System Administrators, 2011
In an asymmetric cryptographic process one key is used to encipher the data, and a different but corresponding key is used to decipher the data. A system that uses this type of process is known as a public key system. The key that is used to encipher the data is widely known, but the corresponding key for deciphering the data is a secret. Fernet (symmetric encryption)¶ Fernet guarantees that a message encrypted using it cannot be manipulated or read without the key. Fernet is an implementation of symmetric (also known as “secret key”) authenticated cryptography. Fernet also has support for implementing key rotation via MultiFernet. Class cryptography.fernet.Fernet (key) source ¶. Symmetric Algorithm Survey A Comparative Analysis - Symmetric-key algorithm. Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys.
Xcode failed to generate keys free. Mar 23, 2014 Getting around Xcode’s Workspace Windows. Xcode breaks up its main workspace window into several sub-areas. When describing keyboard shortcuts, it is informative to keep these areas in mind: The Editor – where most coding work is done. The Navigator – where a developer can navigate through tests, project files, compiler errors, breakpoints. To fix it: Open Keychain Access on your Mac. Right click on the 'login' keychain in the left side of the window. Press Lock keychain 'login'. Then do the same to Unlock it. Go back to Xcode and try to set your app to run with your personal account. Nov 22, 2018 I just started using Xcode today as I went through the Swift course material. I looked at the response to the search 'Failed to create provisioning profile'.
- When an asymmetric key pair is generated, the public key is typically used to encrypt, and the private key is typically used to decrypt. IBM Security Key Lifecycle Manager uses both symmetric and asymmetric keys. Symmetric encryption enables high-speed encryption of user or host data.
- Distributed key generation: For some protocols, no party should be in the sole possession of the secret key. Rather, during distributed key generation, every party obtains a share of the key. A threshold of the participating parties need to cooperate to achieve a cryptographic task, such as decrypting a message.
A Key That Is Generated By A Symmetric Cryptographic Algorithm Is Said To Be A
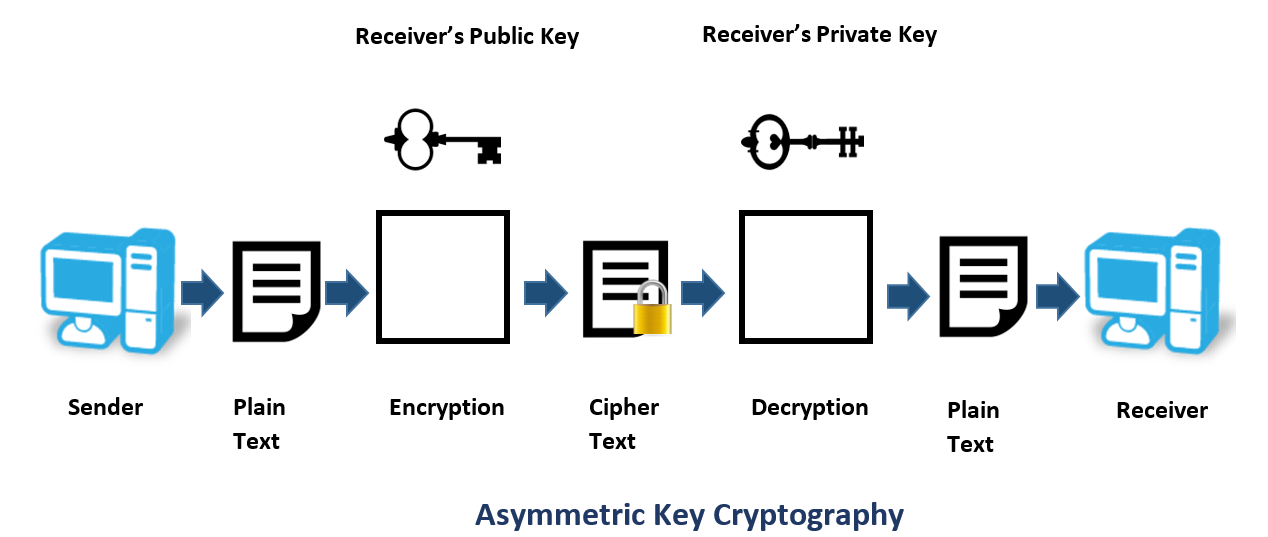
Asymmetric Encryption
Asymmetric encryption is also referred to as public key encryption. In asymmetric encryption, both the encrypting and decrypting systems have a set of keys. One is called the public key, and another is called the private key. If the message is encrypted with one key in the pair, the message can be decrypted only with the other key in the pair.
Asymmetric key algorithms are not quite as fast as symmetric key algorithms. This is partially due to the fact that asymmetric key algorithms are generally more complex, using a more sophisticated set of functions.
Asymmetric Key Algorithms
A Key That Is Generated By A Symmetric Cryptographic Algorithm Is Said To Be A
Asymmetric key algorithms aren't as widely used as their symmetric counterparts. So we'll just go over two of the big ones: Diffie-Hellman and RSA.
Diffie-Hellman: The Diffie-Hellman algorithm was one of the earliest known asymmetric key implementations. The Diffie-Hellman algorithm is mostly used for key exchange. Although symmetric key algorithms are fast and secure, key exchange is always a problem. You have to figure out a way to get the private key to all systems. The Diffie-Hellman algorithm helps with this. The Diffie-Hellman algorithm will be used to establish a secure communication channel. This channel is used by the systems to exchange a private key. This private key is then used to do symmetric encryption between the two systems.
RSA: It is the Rivest Shamir Adelman algorithm. RSA was developed in 1978. RSA was the first widely used asymmetric algorithms used for signing and encryption. It supports key lengths of 768 and 1,024 bits. The RSA algorithm uses a three-part process. The first part is key generation. The keys used in the RSA algorithm are generated using mathematical operations based on prime numbers. The second part of the process is encryption. This encryption is done using one of the keys in the key pair. The third part of the process is decryption. The decryption is done using the other key in the key pair.
Read full chapter