Generate Rsa Key With Password In Argument
- Generate Rsa Key Pair Online
- Crypto Key Generate Rsa
- Generate Rsa Key With Password In Argument Word
- Generate Rsa Key Openssl
- Asymmetric encryption and decryption with RSA. Because RSA can only encrypt messages smaller than the size of the key, it is typically used only for exchanging a random session-key. This session key is used to encipher arbitrary sized data via a stream cipher such as aescbc.
- Feb 09, 2018 The command below will generate the client’s private key and it’s Certificate Signing Request (CSR). The client in this tutorial is called Client2.The script will prompt for a password related.
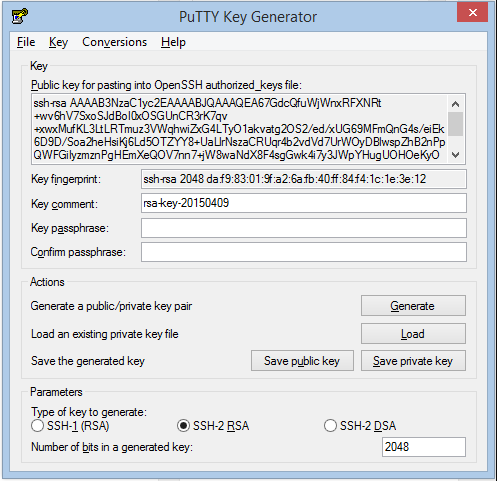
- Usage Guide - RSA Encryption and Decryption Online. In the first section of this tool, you can generate public or private keys. To do so, select the RSA key size among 515, 1024, 2048 and 4096 bit click on the button. This will generate the keys for you.
Generate Rsa Key Pair Online
If you do need to generate an asymmetric signature than can be verified without knowing the password, you're going to have to somehow generate RSA (or DSA, etc.) keys in a deterministic manner based on the password. RSAgeneratekey generates a key pair and returns it in a newly allocated RSA structure. The pseudo-random number generator must be seeded prior to calling RSAgeneratekey. The modulus size will be num bits, and the public exponent will be e. Key sizes with num. The encryption power comes from key bit size or length. In this tutorial we will look how to create 4096 bit keys. Generate 4098 Bit Key. In this example we will generate very secure key. This key size will be 4096 bit. 4096 bit keys are a lot more secure than 2048 or 1024 bit keys.
6.3.3.1 Creating SSL and RSA Certificates and Keys using MySQL
MySQL provides these ways to create the SSL certificate and key files and RSA key-pair files required to support encrypted connections using SSL and secure password exchange using RSA over unencrypted connections, if those files are missing:
The server can autogenerate these files at startup, for MySQL distributions compiled using OpenSSL.
Users can invoke the mysql_ssl_rsa_setup utility manually. Eset nod32 key generator download free. Generate private key openssl windows.
For some distribution types, such as RPM packages, mysql_ssl_rsa_setup invocation occurs during data directory initialization. In this case, the MySQL distribution need not have been compiled using OpenSSL as long as the openssl command is available.
Server autogeneration and mysql_ssl_rsa_setup help lower the barrier to using SSL by making it easier to generate the required files. However, certificates generated by these methods are self-signed, which may not be very secure. After you gain experience using such files, consider obtaining certificate/key material from a registered certificate authority.
For MySQL distributions compiled using OpenSSL, the MySQL server has the capability of automatically generating missing SSL and RSA files at startup. The auto_generate_certs and sha256_password_auto_generate_rsa_keys system variables control automatic generation of these files. These variables are enabled by default. They can be enabled at startup and inspected but not set at runtime.
Crypto Key Generate Rsa
At startup, the server automatically generates server-side and client-side SSL certificate and key files in the data directory if the auto_generate_certs system variable is enabled, no SSL options other than --ssl are specified, and the server-side SSL files are missing from the data directory. These files enable encrypted client connections using SSL; see Section 6.3.1, “Configuring MySQL to Use Encrypted Connections”.
The server checks the data directory for SSL files with the following names:
If any of those files are present, the server creates no SSL files. Otherwise, it creates them, plus some additional files:
If the server autogenerates SSL files, it uses the names of the
ca.pem,server-cert.pem, andserver-key.pemfiles to set the corresponding system variables (ssl_ca,ssl_cert,ssl_key).
At startup, the server automatically generates RSA private/public key-pair files in the data directory if all of these conditions are true: The sha256_password_auto_generate_rsa_keys system variable is enabled; no RSA options are specified; the RSA files are missing from the data directory. These key-pair files enable secure password exchange using RSA over unencrypted connections for accounts authenticated by the sha256_password plugin; see Section 6.4.1.5, “SHA-256 Pluggable Authentication”.
The server checks the data directory for RSA files with the following names:
If any of these files are present, the server creates no RSA files. Otherwise, it creates them.
If the server autogenerates the RSA files, it uses their names to set the corresponding system variables (
sha256_password_private_key_path,sha256_password_public_key_path).
Generate Rsa Key With Password In Argument Word
Manual SSL and RSA File Generation Using mysql_ssl_rsa_setup
MySQL distributions include a mysql_ssl_rsa_setup utility that can be invoked manually to generate SSL and RSA files. This utility is included with all MySQL distributions, but it does require that the openssl command be available. For usage instructions, see Section 4.4.5, “mysql_ssl_rsa_setup — Create SSL/RSA Files”.
SSL and RSA files created automatically by the server or by invoking mysql_ssl_rsa_setup have these characteristics:
SSL and RSA keys are have a size of 2048 bits.
The SSL CA certificate is self signed.
The SSL server and client certificates are signed with the CA certificate and key, using the
sha256WithRSAEncryptionsignature algorithm.SSL certificates use these Common Name (CN) values, with the appropriate certificate type (CA, Server, Client):
The
suffixvalue is based on the MySQL version number. For files generated by mysql_ssl_rsa_setup, the suffix can be specified explicitly using the--suffixoption.For files generated by the server, if the resulting CN values exceed 64 characters, the
_portion of the name is omitted.suffixSSL files have blank values for Country (C), State or Province (ST), Organization (O), Organization Unit Name (OU) and email address.
SSL files created by the server or by mysql_ssl_rsa_setup are valid for ten years from the time of generation.
RSA files do not expire.
SSL files have different serial numbers for each certificate/key pair (1 for CA, 2 for Server, 3 for Client).
Files created automatically by the server are owned by the account that runs the server. Files created using mysql_ssl_rsa_setup are owned by the user who invoked that program. This can be changed on systems that support the
chown()system call if the program is invoked byrootand the--uidoption is given to specify the user who should own the files.On Unix and Unix-like systems, the file access mode is 644 for certificate files (that is, world readable) and 600 for key files (that is, accessible only by the account that runs the server).

To see the contents of an SSL certificate (for example, to check the range of dates over which it is valid), invoke openssl directly:
Generate Rsa Key Openssl
It is also possible to check SSL certificate expiration information using this SQL statement: