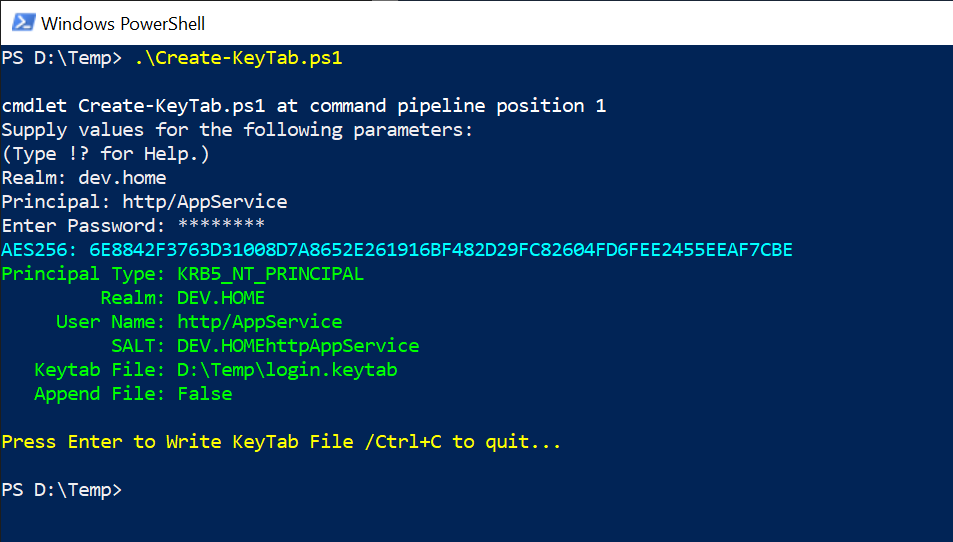
Powershell Generate Aes 256 Key
Powershell Aes Decrypt
| #regionEncryption |
| /// <summary> |
| /// Generate a private key |
| /// From : www.chapleau.info/blog/2011/01/06/usingsimplestringkeywithaes256encryptioninc.html |
| /// </summary> |
| privatestaticstringGenerateKey(intiKeySize) |
| { |
| RijndaelManagedaesEncryption=newRijndaelManaged(); |
| aesEncryption.KeySize=iKeySize; |
| aesEncryption.BlockSize=128; |
| aesEncryption.Mode=CipherMode.CBC; |
| aesEncryption.Padding=PaddingMode.PKCS7; |
| aesEncryption.GenerateIV(); |
| stringivStr=Convert.ToBase64String(aesEncryption.IV); |
| aesEncryption.GenerateKey(); |
| stringkeyStr=Convert.ToBase64String(aesEncryption.Key); |
| stringcompleteKey=ivStr+','+keyStr; |
| returnConvert.ToBase64String(ASCIIEncoding.UTF8.GetBytes(completeKey)); |
| } |
| /// <summary> |
| /// Encrypt |
| /// From : www.chapleau.info/blog/2011/01/06/usingsimplestringkeywithaes256encryptioninc.html |
| /// </summary> |
| privatestaticstringEncrypt(stringiPlainStr, stringiCompleteEncodedKey, intiKeySize) |
| { |
| RijndaelManagedaesEncryption=newRijndaelManaged(); |
| aesEncryption.KeySize=iKeySize; |
| aesEncryption.BlockSize=128; |
| aesEncryption.Mode=CipherMode.CBC; |
| aesEncryption.Padding=PaddingMode.PKCS7; |
| aesEncryption.IV=Convert.FromBase64String(ASCIIEncoding.UTF8.GetString(Convert.FromBase64String(iCompleteEncodedKey)).Split(',')[0]); |
| aesEncryption.Key=Convert.FromBase64String(ASCIIEncoding.UTF8.GetString(Convert.FromBase64String(iCompleteEncodedKey)).Split(',')[1]); |
| byte[] plainText=ASCIIEncoding.UTF8.GetBytes(iPlainStr); |
| ICryptoTransformcrypto=aesEncryption.CreateEncryptor(); |
| byte[] cipherText=crypto.TransformFinalBlock(plainText, 0, plainText.Length); |
| returnConvert.ToBase64String(cipherText); |
| } |
| /// <summary> |
| /// Decrypt |
| /// From : www.chapleau.info/blog/2011/01/06/usingsimplestringkeywithaes256encryptioninc.html |
| /// </summary> |
| privatestaticstringDecrypt(stringiEncryptedText, stringiCompleteEncodedKey, intiKeySize) |
| { |
| RijndaelManagedaesEncryption=newRijndaelManaged(); |
| aesEncryption.KeySize=iKeySize; |
| aesEncryption.BlockSize=128; |
| aesEncryption.Mode=CipherMode.CBC; |
| aesEncryption.Padding=PaddingMode.PKCS7; |
| aesEncryption.IV=Convert.FromBase64String(ASCIIEncoding.UTF8.GetString(Convert.FromBase64String(iCompleteEncodedKey)).Split(',')[0]); |
| aesEncryption.Key=Convert.FromBase64String(ASCIIEncoding.UTF8.GetString(Convert.FromBase64String(iCompleteEncodedKey)).Split(',')[1]); |
| ICryptoTransformdecrypto=aesEncryption.CreateDecryptor(); |
| byte[] encryptedBytes=Convert.FromBase64CharArray(iEncryptedText.ToCharArray(), 0, iEncryptedText.Length); |
| returnASCIIEncoding.UTF8.GetString(decrypto.TransformFinalBlock(encryptedBytes, 0, encryptedBytes.Length)); |
| } |
| #endregion |
- Jan 04, 2017 In this post we will see how we can Generate MachineKey using Windows PowerShell from local development machine. The property in web.config file configures algorithms and keys to use for encryption. We will use a PowerShell script to create this machineKey. Here’s the Powershell Script.
- Oct 31, 2007 PowerShell Script for AES Key Generation I have to constantly generate AES keys for the numerous SSO requests that we receive from our clients. The keys are used for message level security, and they're really the biggest headache we have when it comes to setting up SSO for a new client.
- You may also find it useful to generate another key for HMAC, so you can verify that the encrypted files haven't been tampered with. If you want to do that, you can generate a 128-bit HMAC key, and encrypt and store that with the main AES key.
- Today's topic is encrypting with AES 256. While the AES class is very straight forward to use. The generation of the key is not. Here are some mistakes to avoid: Do not use only Text.Encoding::UTF8.GetBytes to generate the key this weakens the encryption by reducing the entropy space. Do not just get the has of the key.
So a value must generate the same encrypted string each time it is encrypted. Currently I'm using a 32 char key working on the possibly incorrect assumption this is 256 bits? So, I would want 'the quick brown fox' to be converted to a suitable AES 256 bit key?
commented Jun 6, 2014
hi fairly new to the cryptography.. please suggest a resolution |
Aes 256 Java
commented Oct 9, 2017 • edited
edited
Fips 140-2
How-to save -safely- the private key ? Windows registry ? in disk ? I use ASP.NET applications. Test your code |
In this post we will see how we can Generate MachineKey using Windows PowerShell from our local development machine.
Problem:
Many a times when a ASP.Net application is running on production server, we get an error message stating – “Validation of viewstate MAC failed. If this application is hosted by a web farm or cluster, ensure that <machineKey> configuration specifies the same validationKey and validation algorithm. AutoGenerate cannot be used in a cluster.” This error happens because of missing machineKey property in the web.config file.
Overview:
The <machineKey> property in web.config file configures algorithms and keys to use for encryption, decryption, and validation of forms-authentication data and view-state data, and for out-of-process session state identification.This encryption prevents tempering of session data on the server. It is present under <system.web> node in web.config file and looks like below –
Powershell Aes Encryption
N.B: Do not use this machineKey on your production servers. Instead follow the steps mentioned below to generate a new one only for you.
Solution:
We will use a PowerShell script to create this machineKey. Here’s the Powershell Script
You can save this PowerShell script as “generateMachineKey.ps1” on your hard disk. Now open Windows Powershell and perform the following steps –
- Go to the folder where you have stored the .ps1 file
- Load the Script
- Call the PowerShell Function
This will give you a new machineKey. You can copy this and paste it on to your web.config file now.
Hope you like this post.