Generate Ssh Key Ubuntu Digitalocean
DigitalOcean is a cloud infrastructure provider with a user-friendly UI that creates and manages virtual infrastructure. DigitalOcean refers to the virtual servers provided as droplets. This is the general workflow for protecting a DigitalOcean droplet behind Cloudflare Access.
- Ubuntu Add Ssh Key
- Create New Ssh Key
- Ubuntu Ssh Public Key No Password
- Generate Ssh Key Putty
- Generate Ssh Key Ubuntu Digitalocean Free
May 05, 2014 Install putty and generate ssh key to auto log in to Ubuntu server 14 Table of contents: 1. Install putty and generate ssh key to auto log in to Ubuntu server 14. DigitalOcean 48,590 views. How to set up passwordless SSH access for root user duplicate. I revised the answer to address both issues as this question is linked as how to generate a paswordless ssh key (due to poor title). You must configure the sudoers file without having to fiddle with /etc/ssh/sshdconfig. See How to make Ubuntu remember forever the password.
Create your droplet
Dec 18, 2019 How to Set Up SSH Keys on Ubuntu 18.04. Secure Shell (SSH) is a cryptographic network protocol used for a secure connection between a client and a server and supports various authentication mechanisms. The two most popular mechanisms are passwords based authentication and public key based authentication. Apr 15, 2017 In this video, I’m going to show you how to quickly generate an SSH Key on our Mac. This will allow you SSH access to your DigitalOcean Droplet – or any other type of dedicated server. DigitalOcean: public keys get replaced by an obscure key on every reboot. The keys in the 'authorizedkeys' file under /root/.ssh get deleted and a strange. I can't seem to log in to my droplet on digitalocean. When I try ssh root@162.243.134.123 I get a Permission denied (publickey). I tried resetting the root password and logging in via the digita.
After you log in to your DigitalOcean account:
- On your DigitalOcean dashboard, click Create > Droplets.
The Create Droplets dialog displays.
You can use a droplet of any size and a plan of any time. Cloudflare Access SSH has GA support for servers with x86, AMD64 and ARMv6 architectures. The instructions in this document use Ubuntu. You do not need to select additional options, such as Private Network or Add SSH keys to proceed.
- Click Create at the top-right of the Create Droplets window.
Configure your droplet
Once created, DigitalOcean provides a temporary public IP address to use to reach your droplet to configure Cloudflare Access. DigitalOcean sends you an email with the initial root password.
- Copy the password from the email and use the IP the following command:
Run the command from your local terminal, replacing the demo IP with the IP from DigitalOcean for your droplet.
The output confirms the SSH connection to your droplet.
- In the root password field, paste the password sent in the DigitalOcean email.
- Complete the new password request.
- Securely save your new password.
Ubuntu Add Ssh Key
Now, let’s set up an Access policy.
Create an Access policy
Cloudflare Access controls who reaches your resource by evaluating every request made to that destination for authentication in the form of a JSON Web Token (JWT). Cloudflare generates this token based on a login event with the configured IdP.
To use Access, you must have at least one registered domain using its authoritative Domain Name System (DNS) on Cloudflare. You can then generate subdomains to represent the resources protected by Access. We use the domain widgetcorp.tech in our example; the subdomain droplet.widgetcorp.tech represents the DigitalOcean droplet. You don’t need to configure DNS for that subdomain at this time.
To create an Access policy:
- Login to your Cloudflare dashboard and navigate to the Access app.
- In the Access Policies section, click Create Access Policy.
- Enter the subdomain that represents the resource to protect with Access.4 (optional) Configure rules to allow members of your organization to reach this subdomain in the Policies section.
In our example, the policy allows anyone with an @cloudflare.com email address to reach the machine.
- Click Save.
Generate a certificate public key
You generate a public key to validate certificates presented during the SSH session, and issue them to cloudflared.
Note: Your origin can use these short-lived certificates as an alternative to SSH keys for validating requests.
- On the Access app in your Cloudflare dashboard, navigate to the Short-Lived Certificates card.
- Click the Select an app drop-down list and select the name of the application you created in from the drop-down menu.
- Click Generate certificate.
The new public key displays.
- Click Copy to place public key on your clipboard.
This public key is now always available on this page.
Match Unix usernames to SSO IDs
Cloudflare Access takes the identity from a token and short-lived certificates to authorize the user. Access matches rely on the identity that precedes an email domain. For example, if the user identity in your Okta or GSuite IdP is [email protected], Access attempts to match that identity to the Unix user jdoe.
Return to the SSH session with your droplet to complete this step. Our example user is [email protected], which matches the Access policy because the identity belongs to the @cloudflare.com domain.
In a terminal window, issue the following command to ensure that a corresponding Unix user exists:
There’s a track on cloud security, and you can be sure cloud will be an underlying theme in several other tracks. There’s no question that the recent flood of news regarding corporate data security breaches and the need for significantly better policies to protect personal information are just a couple of the reasons why this event could not be more timely and relevant. With tracks spanning the whole spectrum of interests-from the C-suite perspective to critical decisions regarding technology infrastructure-every aspect of security will be covered at the conference. As more organizations move to a cloud strategy, a primary concern is how to ensure and, more specifically, how and where data and encryption keys are managed in order to minimize the threat of a data breach.HSM security: Great for on-premise, but need alternatives for the cloudOrganizations that host data and applications on-premise often employ HSM security, the physical hardware security modules that manage keys for authentication and data encryption, and have confidence in the level of security provided. HSMs are typically certified to Common Criteria or FIPS-140-2 standards for product design, implementation, and cryptographic algorithms. Risk if hsm is not used to generate encryption key download.
Save your public key
Now we’ll save the public key previously generated by Access as a new PUB file on your system.
- In the terminal, change directories to the SSH configuration directory on the machine:
- Generate the file and open a text editor to input the public key:
- Ensure that you are in insert mode (
i) and paste the public key in the new file.
Important: Do not modify any other content.
- Save the file (
:wq).
Note: Command use may depend on your permissions. Some systems require this command to force save and quit:
Modify your SSHD Configuration
Cloudflare Access requires two changes to the sshd_config file on the target machine. The first change requires uncommenting a field already set in most default configurations; the second change adds a new field.
To modify the sshd_config file:
- In the terminal window, stay in the
/etc/sshdirectory and open thesshd_configfile:
- Navigate to the
PubkeyAuthenticationrow.
In most default configurations, the row appears uncommented. This example shows it commented out using the hash ( # ) symbol:
- Enter insert (
i) mode, and delete the hash symbol to uncomment the line.
Note: Make no other changes.
- Insert this new line below
PubkeyAuthentication:
This adds the public key you previously saved to authorize users to your SSH configuration.
- Save the file (
:wq).
Note: Command use may depend on your permissions. Some systems require this command to force save and quit:
Restart the SSH server
After modifying your SSHD configuration, restart the SSH service on the machine. Our example is for servers running systemd, as well as systemctl. Execute both commands:
Configure Argo Tunnel
Argo Tunnel is a Cloudflare feature that uses a lightweight daemon, cloudflared, to securely connect your server to the Cloudflare network using only outbound calls. Each Argo Tunnel consists of multiple, highly available connections to at least two Cloudflare data centers.
Review these instructions for setting up Argo Tunnel.
Create Your Argo Tunnel
You first create the subdomain that represents your machine. When Access authenticates a request, cloudflared proxies requests to that subdomain through the Cloudflare network to port 22 on the server.
Run the following command to create the Argo Tunnel and subdomain. You do not need to manually configure DNS records in the Cloudflare dashboard:
Note: This example uses a nohup prefix to keep the Argo Tunnel running after the session terminates. Production use cases may need to run cloudflared as a systemd process. Read more about running cloudflared in production environments in these guidelines. The output should resemble this:
You can confirm that the DNS record was created by visiting the DNS page in the Cloudflare dashboard for the domain.
Configure your Client SSH connection
On the client side, follow the instructions in Connecting over SSH to configure the device to use Cloudflare Access to reach the protected machine. To use short-lived certificates, include the following settings in the SSH configuration file:
You can save time by printing the configuration required for your specific instance with the following cloudflared command:
Test your SSH configuration by running this command from your local terminal:
cloudflared launches a browser window and prompts for authentication with your IdP. On success, Access generates a JWT (JSON Web Token) and a short-lived certificate, and authorizes the user into the server.
Lock down all ingress
In this example, cloudflared only makes outgoing calls to the Cloudflare network for the droplet.widgetcorp.tech hostname. With that, you can restrict all ingress to the machine to secure the server in case the origin IP is ever exposed.
To lock down ingress in DigitalOcean:
- Select your droplet and pick Networking from the sidebar.
- Scroll to the bottom of the page and click Create Firewall.
- In the next screen, remove any rules that allow ingress to the server.
When no rules are listed DigitalOcean restricts all ingress. You must keep egress open.
- Select the droplet name where this rule applies, and click Create Firewall.
Ingress to the droplet is now locked down.
An SSH Key allows you to log into your server without needing a password. SSH Keys can be automatically added to servers during the installation process.
Create New Ssh Key
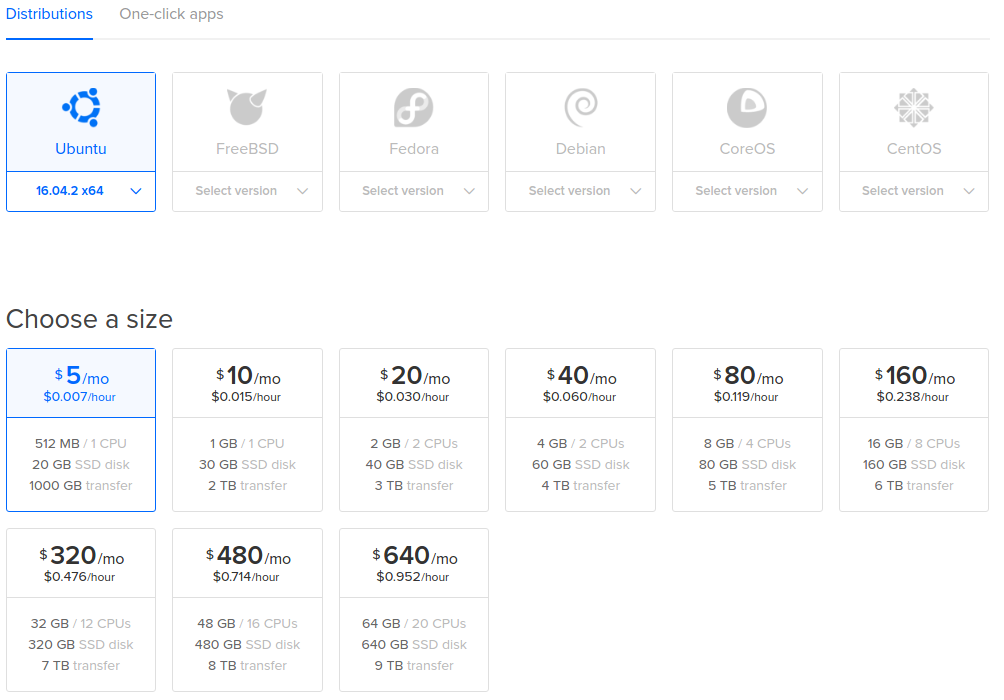
Creating an SSH key on Windows
The simplest way to create SSH key on Windows is to use PuTTYgen.
Ubuntu Ssh Public Key No Password
- Download and run PuTTYgen.
- Click the 'Generate' button.
- For additional security, you can enter a key passphrase. This will be required to use the SSH key, and will prevent someone with access to your key file from using the key.
- Once the key has been generated, click 'Save Private Key'. Make sure you save this somewhere safe, as it is not possible to recover this file if it gets lost
- Select all of the text in the 'Public key for pasting into OpenSSH
authorized_keysfile'. This is what you would need to enter into the control panel to use the SSH key.
Creating an SSH key on Linux
Generate Ssh Key Putty
The tools to create and use SSH are standard, and should be present on most Linux distributions. With the following commands, you can generate ssh key.
- Run:
ssh-keygen -t rsa. For a more secure 4096-bit key, run:ssh-keygen -t rsa -b 4096 - Press enter when asked where you want to save the key (this will use the default location).
- Enter a passphrase for your key.
- Run
cat ~/.ssh/id_rsa.pub- this will give you the key in the proper format to paste into the control panel. - Make sure you backup the
~/.ssh/id_rsafile. This cannot be recovered if it is lost.
Adding an SSH key to your control panel
- Once you're logged in, go to https://my.vultr.com/sshkeys.
- Click 'Add SSH Key'.
- Enter a descriptive name for the key.
- Paste in your SSH public key. This is a long string beginning with 'ssh-rsa'. You should have saved this from when you generated your key.
- Click 'Add SSH Key'.
- Now, when you're deploying servers you will be able to select which SSH keys you want to add to the newly deployed server. Remember to select the keys before the initial server deployment, otherwise you will need to log into the newly created server and add the SSH keys manually.
Limitations
- SSH keys are only available for Linux and FreeBSD. They are not supported for Windows, custom ISOs, nor snapshot restores.
- SSH keys can only be managed from the control panel during deployment. You cannot use the control panel to manage them on an already-installed instance.
Connecting to a server using an SSH key from a Windows client
- Download and run the PuTTY SSH client.
- Type the IP address or Username + IP address (
user@x.x.x.x) of the destination server under the 'Host Name' field on the 'Session' category. - Navigate to the 'Connection -> SSH -> Auth' category (left-hand side).
- Click 'Browse..' near 'Private key file for authentication'. Choose the private key file (ending in
.ppk) that you generated earlier with PuTTYgen. - Click 'Open' to initiate the connection.
- When finished, end your session by pressing
Ctrl+d.
Generate Ssh Key Ubuntu Digitalocean Free
Connecting to a server using an SSH key from a Linux client
- Check that your Linux operating system has an SSH client installed (
which ssh). If a client is not installed, you will need to install one. - Initiate a connection:
ssh -i /path/to/id_rsa user@x.x.x.x - When finished, end your session by pressing
Ctrl+d.